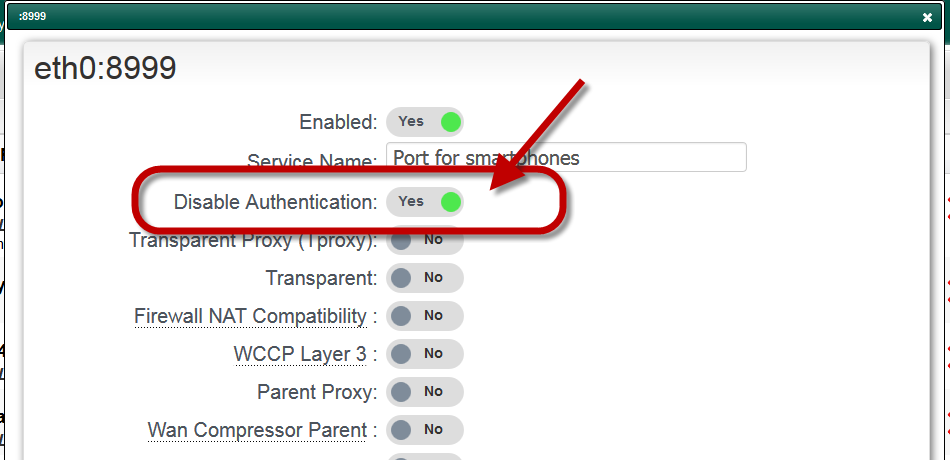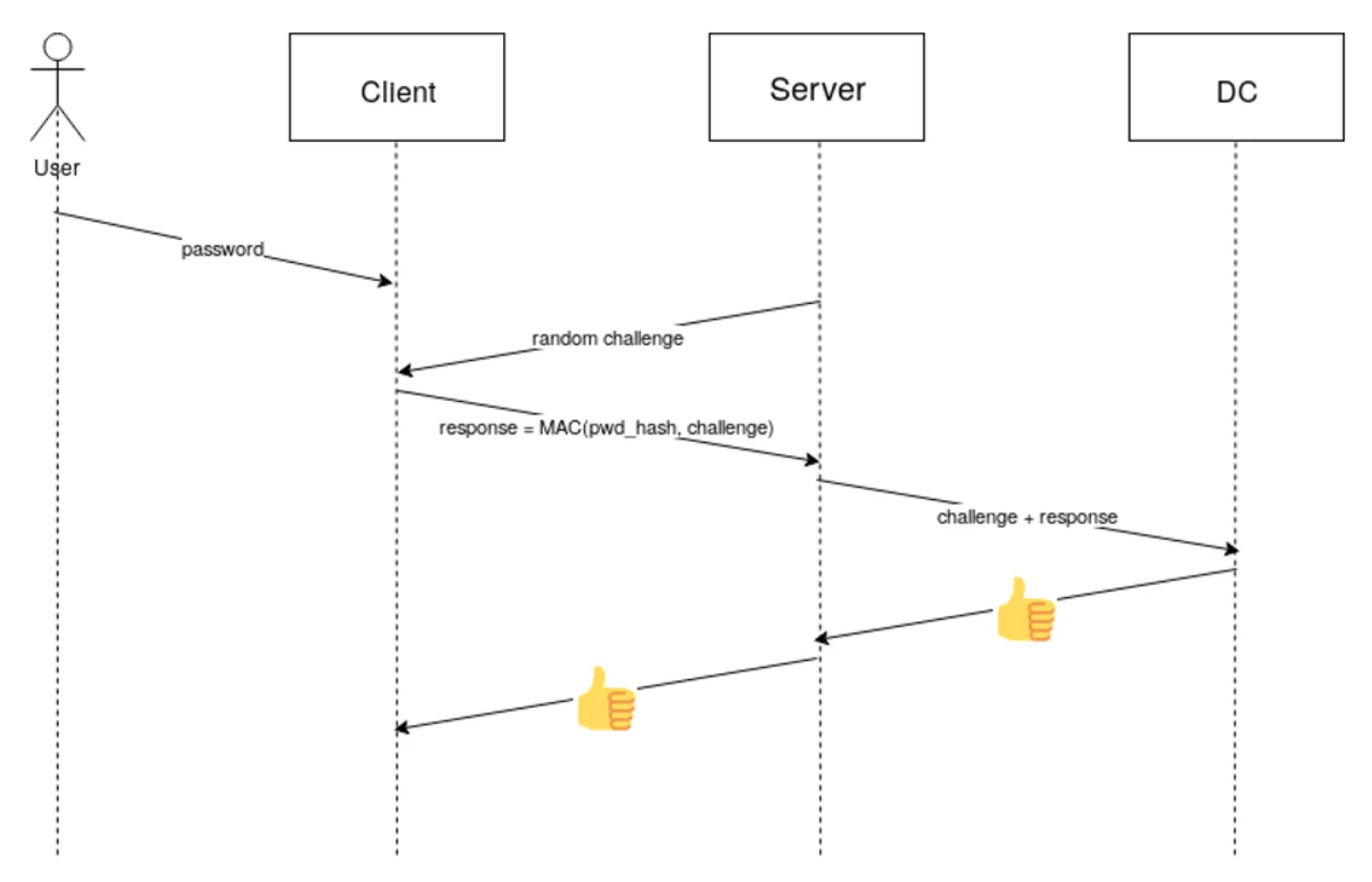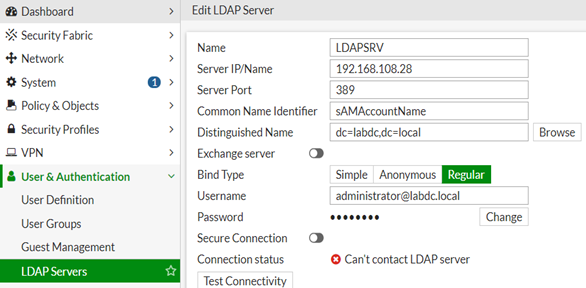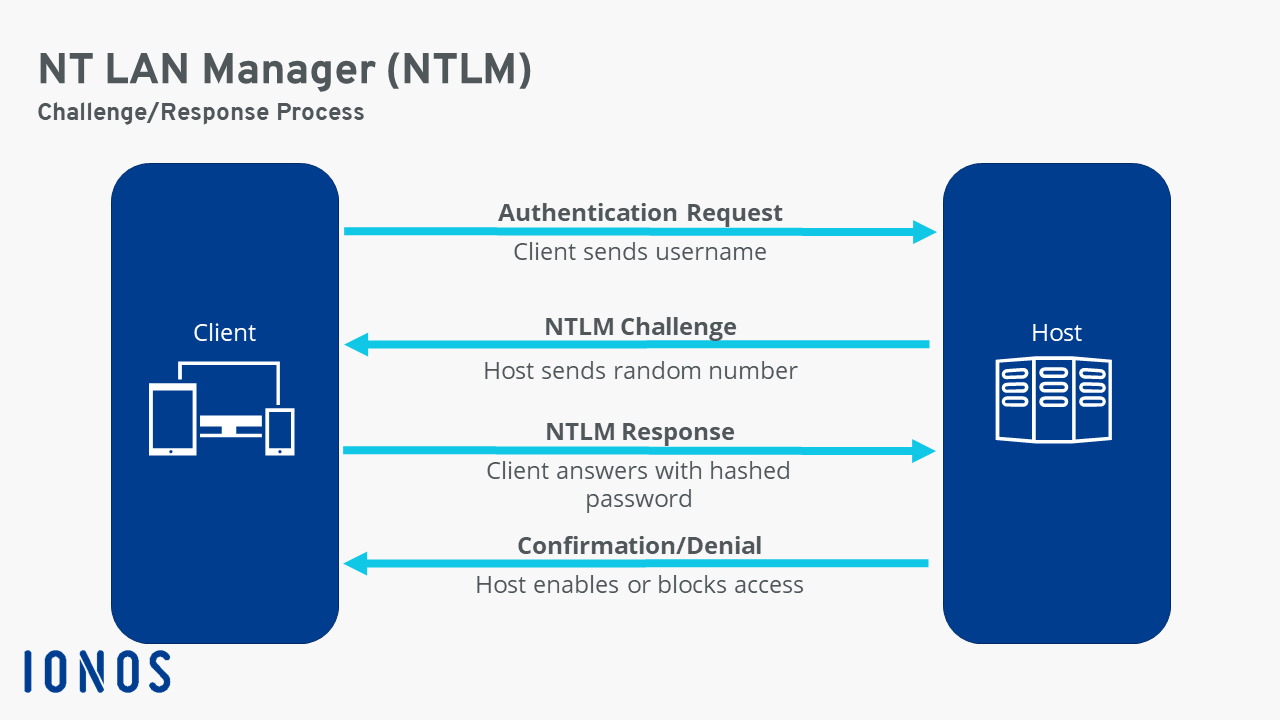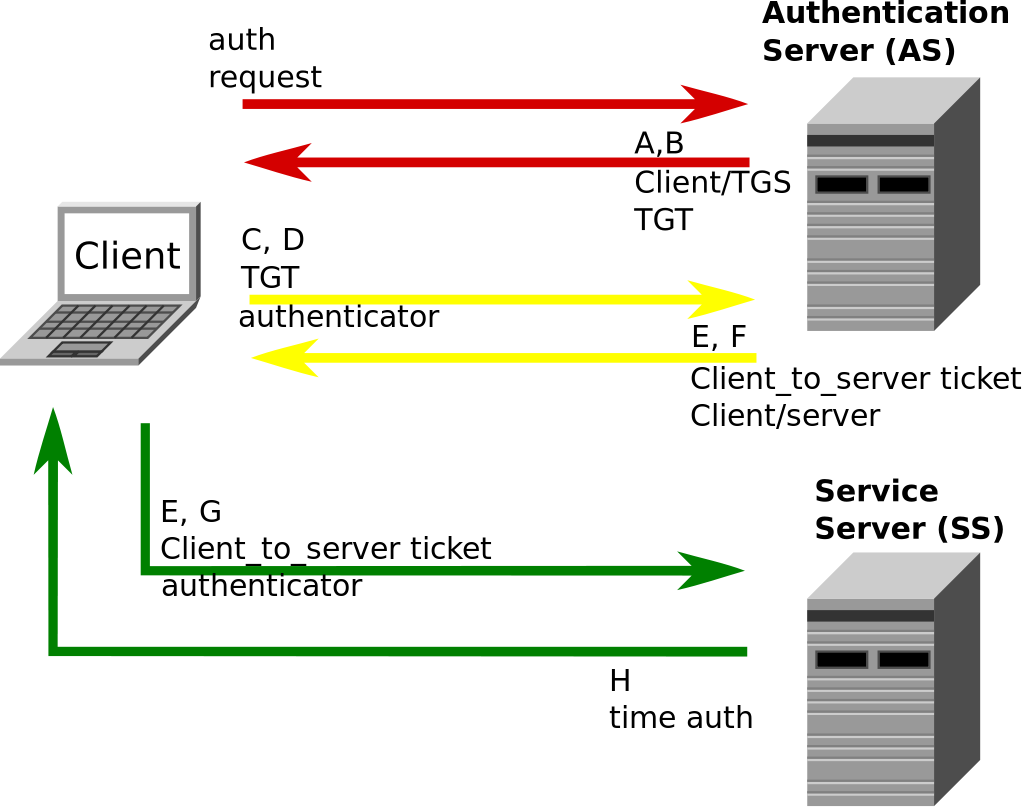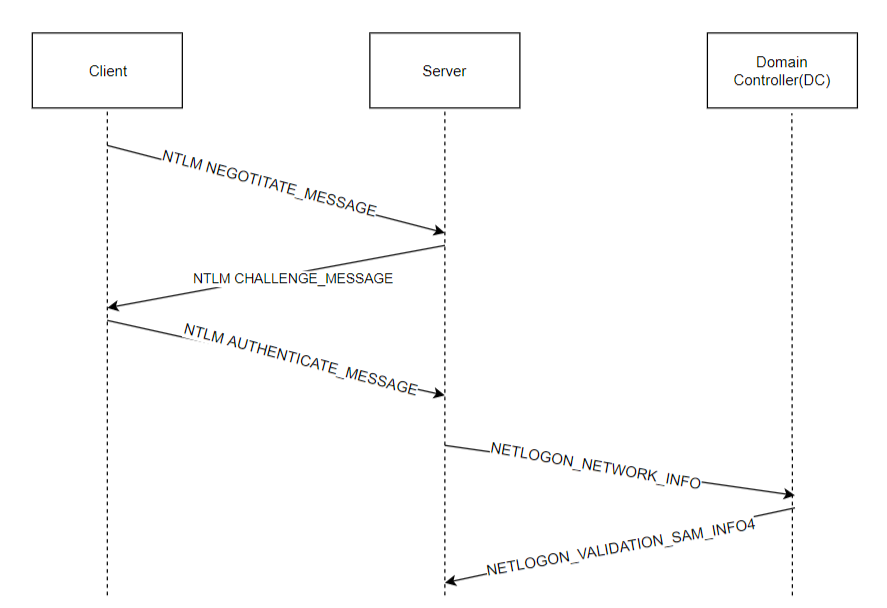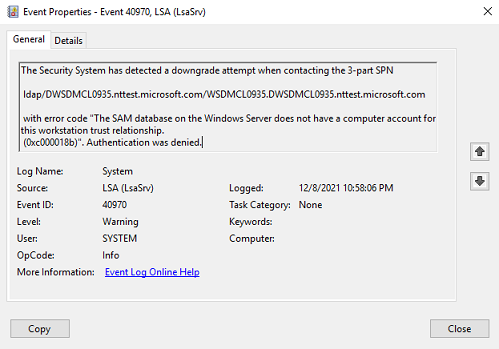
KB5011233: Protections in CVE-2022-21920 may block NTLM authentication if Kerberos authentication is not successful - Microsoft Support

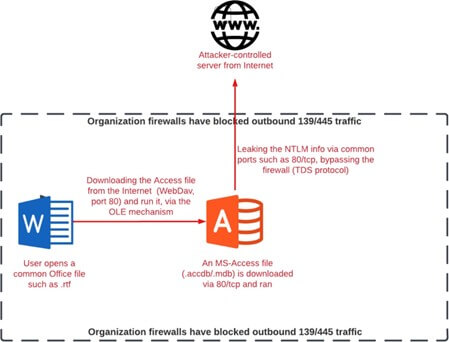
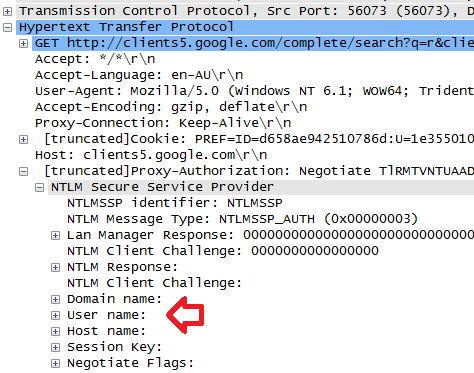
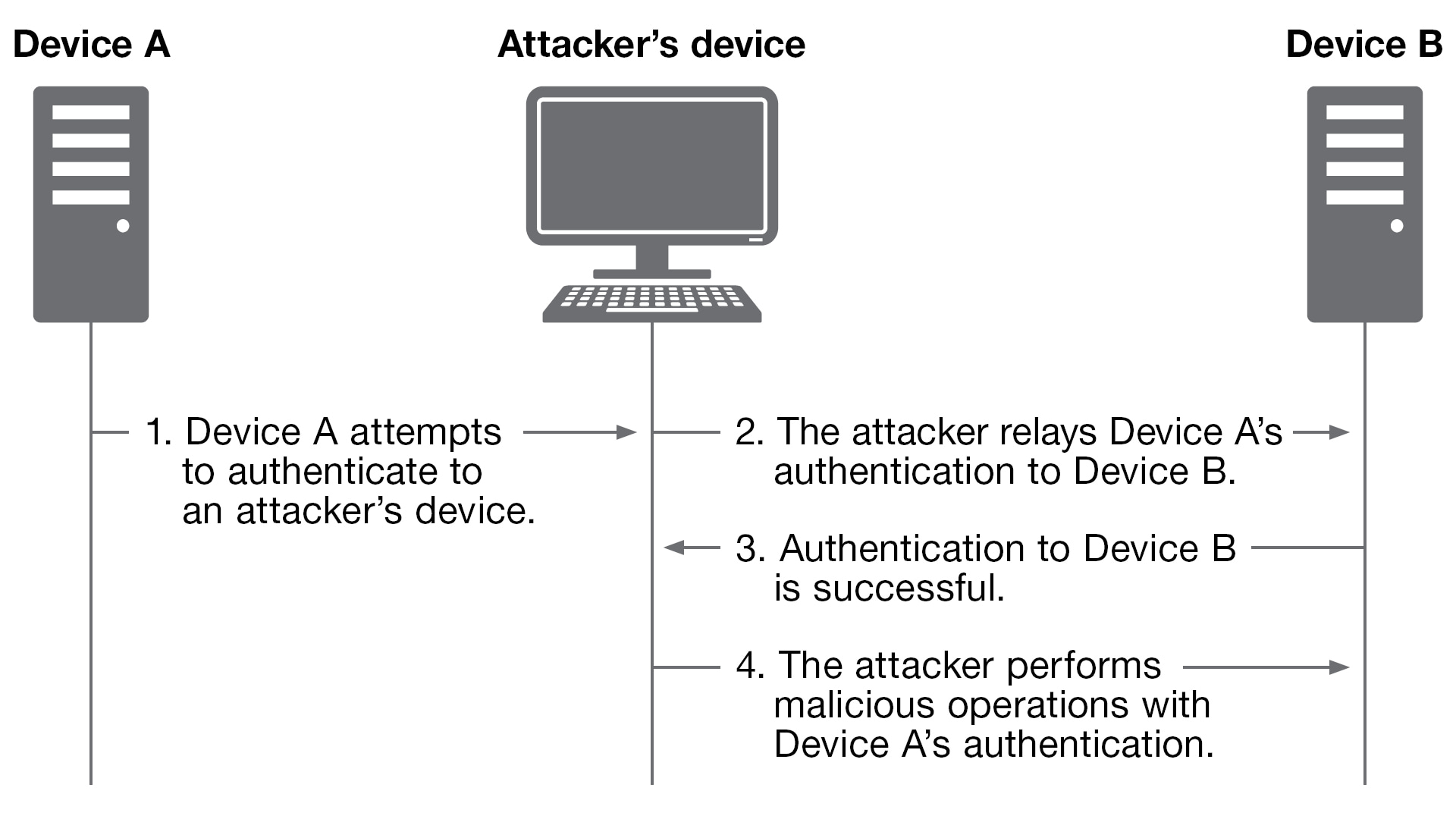
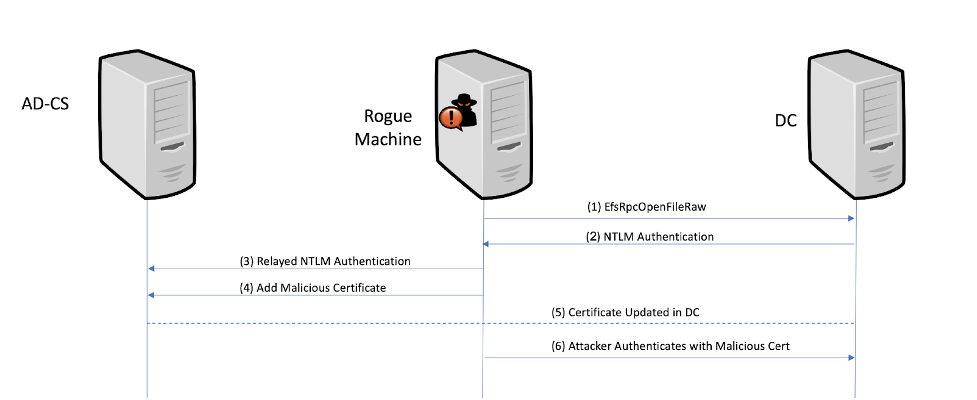
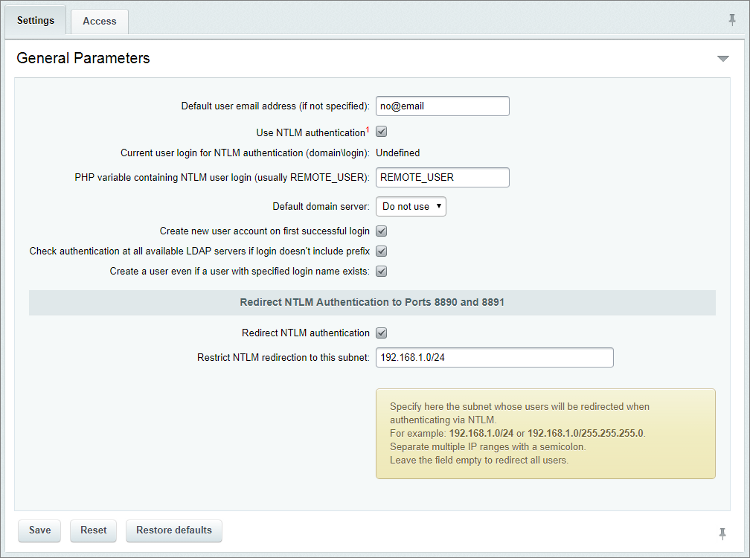
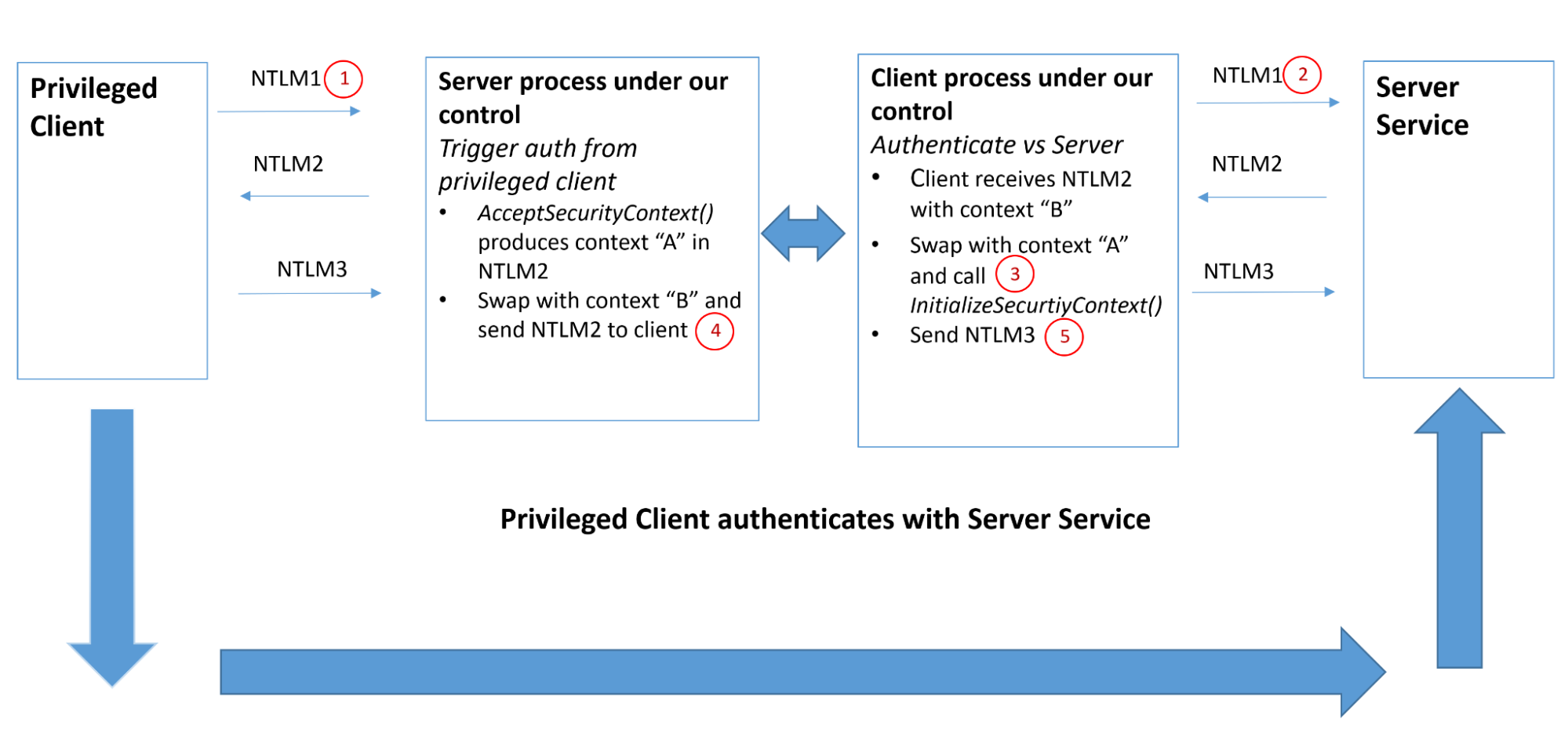
Internal Information Disclosure using Hidden NTLM Authentication | by Mike Brown | The Startup | Medium